Protect company data on smartphones & tablets!
Most people nowadays use a smartphone daily, and quite a few of them also use it for business purposes. Be it to write emails, make phone calls, sign PDFs, or occasionally adapt documents or presentations. The latter tends to be done with a tablet. However, those are treated identically to smartphones from an IT perspective. Since these devices are mostly privately owned, many private apps are on them. Hence a user can easily download a potentially sensitive document with crucial corporate data from the business mail account and share it with any app (like WhatsApp or Dropbox). Thus, the company loses control over the company's data or, in the worst-case scenario, even gives the rights to other companies. The so-called "App protection policies" can be used to prevent this risk. The following article will illustrate how those policies work in practice using iOS screenshots.
App Protection Policies
With "App protection policies", a company can protect its internal organizational data. This method is particularly suitable for a "Bring Your Own Device" strategy, i.e. the user uses his device to access corporate resources. This solution's significant advantage is that the user has to do almost nothing on his device. As soon as they log into an app, e.g. Outlook or Teams, they are prompted once to download the "Microsoft Authenticator" app.

As soon as one has logged into a Microsoft app, the set of policies takes effect. The corresponding message confirms it:
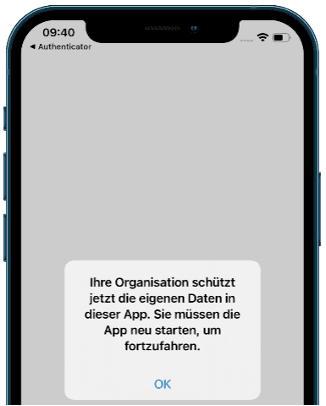
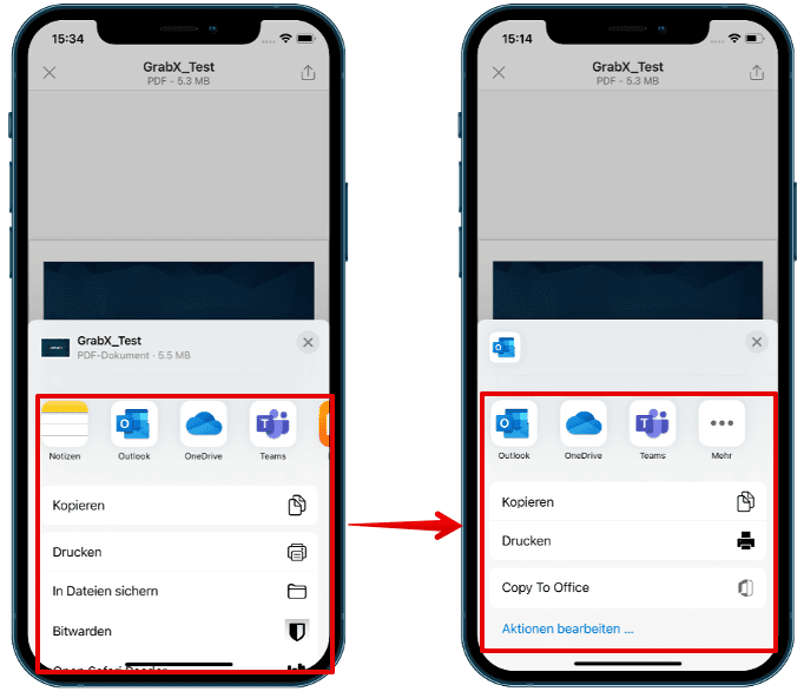
Try to share an attachment from Outlook to a non-managed app to test the policy. These apps should not even appear in the "Share" dialogue box as shown in the following pictures:
Microsoft Endpoint Manager (MEM)
I'll now show you what this configuration looks like in the MEM Admin Center and the diverse available options. All policies are configured under the "App protection policies" pannel for iOS and Android. However, each operating system needs a distinct policy. In the following example, I'll create such a policy for iOS (the policy for Android would be almost identical):
If you wonder whether such policies also exist for macOS or Windows, I have to disappoint you. Unfortunately, this option only exists for smartphones. For completeness, I nevertheless have to say that there is a similar possibility for Windows with WIP (Windows Information Protection).
While creating an "App protection policy" you'll be confronted with several options, and I will briefly describe the most important ones below.
Apps
Firstly, you can choose the device types and apps which should be protected. I recommend selecting "All" device types and at least all Microsoft apps for the apps. I personally also find the Adobe Acrobat Reader very practical because the user can hence sign a PDF on a tablet or send it back filled out:
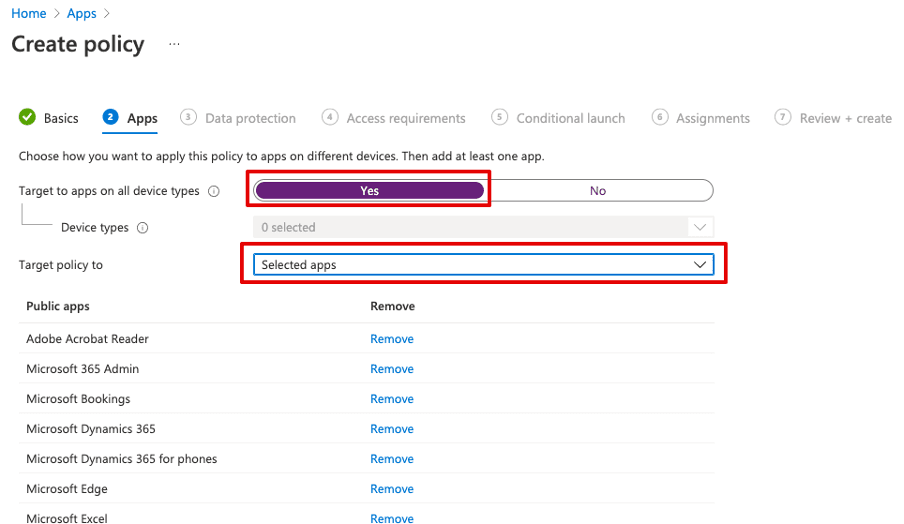
The apps which can be protected are constantly updated and listed under the following link: https://docs.microsoft.com/en-us/mem/intune/apps/apps-supported-intune-apps.
Data Protection
The "Data protection" tab allows you to set up the actual restrictions. The following recommendations are intended as a possible solution and are by no means "THE right solution" for every company:
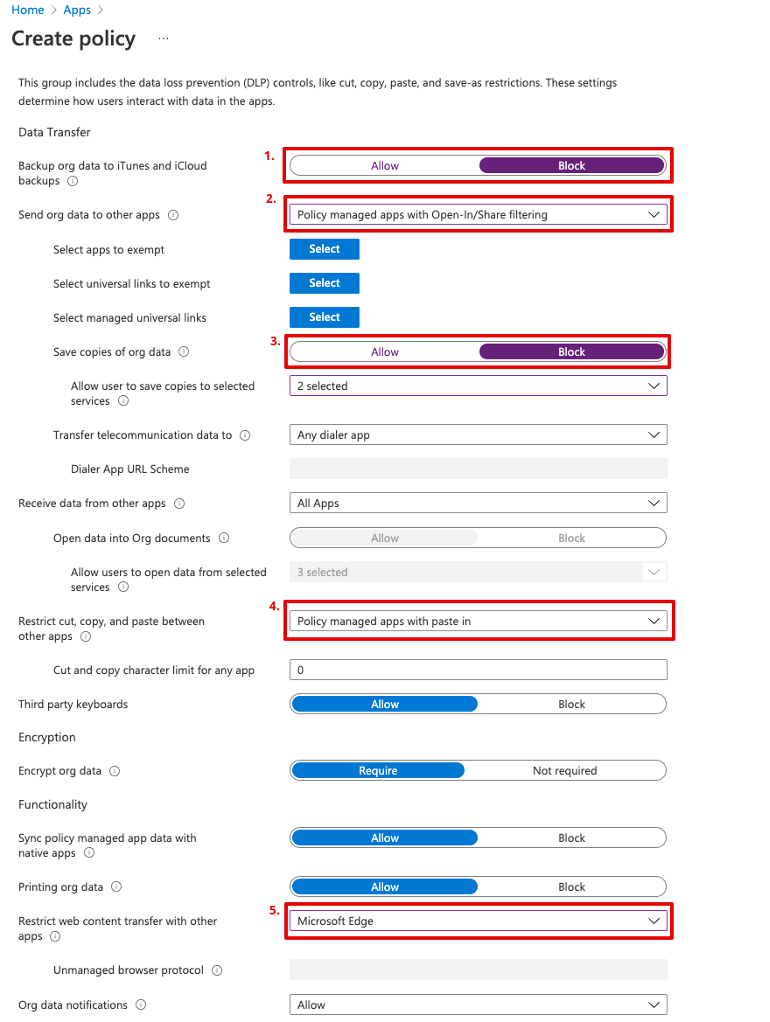
Block: So that no corporate data is backed up to the iCloud.
Policy managed apps with Open-In/Share filtering: So that attachments can only be opened with managed apps, and private apps do not even appear in the "Share" dialogue.
Block - Select SharePoint and OneDrive: So that attachments and other Office documents can only be saved to the company's SharePoint and OneDrive account.
Policy managed apps with paste in: So that no content can be copied and pasted from managed apps into private apps like WhatsApp and co. to Outlook and co., but the reverse way is allowed.
Microsoft Edge: So that links can only be opened in Microsoft Edge and not in Safari or Chrome.
Access requirements
In the next tab, "Access requirements", you need to think precisely about what you want to set. For a simple reason: at this point, you'll select whether a code query is required when a managed app is opened before the user is given access to the app's data (e.g. emails). Additional protection against unauthorized access can therefore be activated with this option. However, it can also annoy and confuse users, as this code has nothing to do with the device code. However, if the devices are not fully managed and only the "App protection policies" are used, the device code could theoretically be disabled. If the device is lost or stolen, the stranger could view all business data without any problems. Therefore, here is a possible solution:
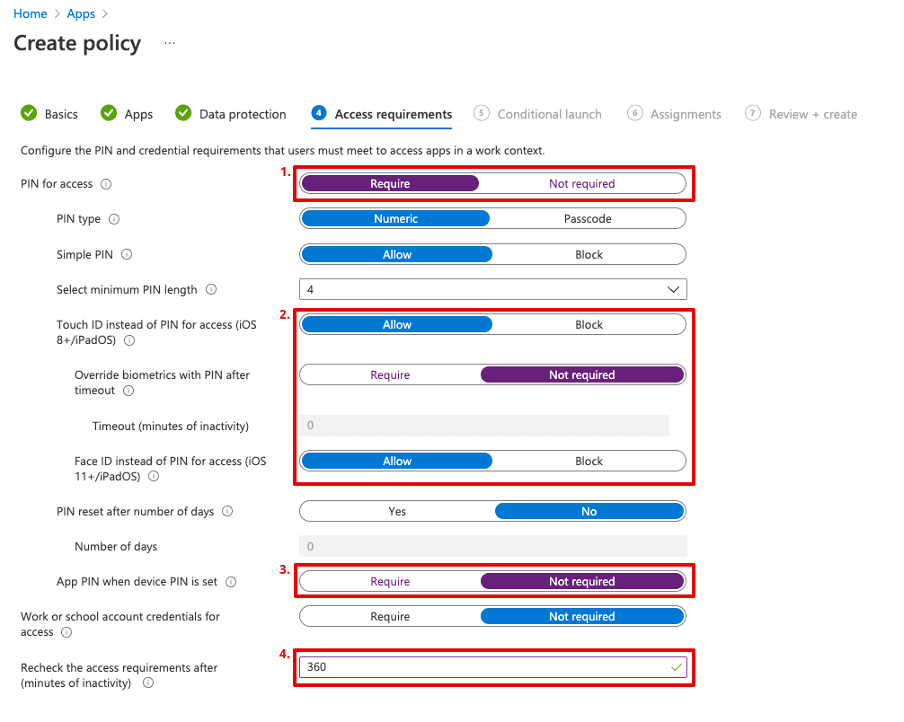
Require: So that a PIN (code) must be set
Allow, not required, Allow: To allow biometric authentication. Allowing it makes it easier for the user and is, therefore, a good compromise.
Not required: If the device is managed and a device code is set, this PIN is disabled.
360 minutes (3 hours): After this time, the user must authenticate again. In between, the user can open the app without a PIN. This setting ensures that the PIN "only" needs to be entered 2-3 times a day during working hours.
Conditional launch
In the tab "Conditional launch" further essential parameters can be set:
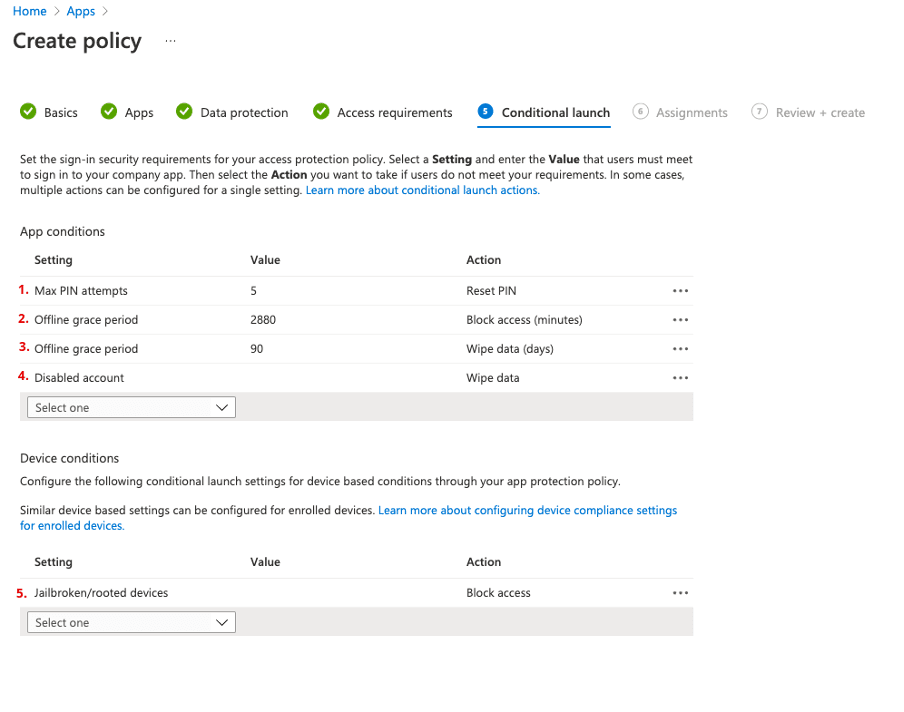
After the set number of incorrect PIN entries, the user must define a new one. For this, you have to re-authenticate with the user's password, and then you can generate a new PIN.
This value defines the time during which the managed data can be accessed offline in the app. After this period, the device must go back online for a short time to ensure that everything is correct and that the device has not been stolen or lost.
After reaching this number of days without an internet connection, all business data will be removed from the apps.
When an account is locked, all data in the protected apps are also removed.
If the device has been jailbroken (software manipulation of iOS), access to the apps will be blocked.
Assigning policies and tests
You can then assign the policy you've just created to the appropriate users in the last tab. It is best to distribute these to a test group first before rolling them out to the whole company.
Summary
With the help of "App protection policies", it is relatively easy to protect business data on smartphones. Users are hardly disturbed in their daily work. Therefore, I would recommend this step to any company. If any questions or suggestions have arisen during your reading, I will be happy to answer them or give a free demo.
